You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Apple Plans Update to Address MacDefender Malware
- Thread starter REWahoo
- Start date
Moemg
Gone but not forgotten
The most amazing thing about the CFB posting is his ignore poster list must have expired so he could finally see a post to respond to !
Koolau
Give me a museum and I'll fill it. (Picasso) Give me a forum ...
The most amazing thing about the CFB posting is his ignore poster list must have expired so he could finally see a post to respond to !
I just figured CFB had hit the "ignore all" button.
Seriously, good to hear from the bunny. Glad he's at least checking up on us from time to time.
Bestwifeever
Moderator Emeritus
- Joined
- Sep 17, 2007
- Messages
- 17,774
Maybe a little snapshot of Gabe the next time you peek out of the rabbit hole, CFB?
Darryl
Full time employment: Posting here.
- Joined
- Mar 29, 2007
- Messages
- 577
CFB, great to hear from you. Glad all is going well!
M Paquette
Moderator Emeritus
Apple has released Security Update 2011-003 which adds blocking of the MacDefender trojan app variations.
About Security Update 2011-003
The update can be automatically found and installed using the Software Update... item from the Apple menu, or can be downloaded and manually installed from the above link.
The installation process will also search for and remove known variants of the MacDefender trojan.
About Security Update 2011-003
The update can be automatically found and installed using the Software Update... item from the Apple menu, or can be downloaded and manually installed from the above link.
The installation process will also search for and remove known variants of the MacDefender trojan.
arebelspy
Full time employment: Posting here.
- Joined
- Apr 26, 2011
- Messages
- 625
Update does nothing, virus already has a workaround that defeats Apple's update.
http://apple.slashdot.org/story/11/...aign=Feed:+slashdot/eqWf+(Slashdot:+Slashdot)
lol
Whichever side of the debate you're on, that's just funny.
http://apple.slashdot.org/story/11/...aign=Feed:+slashdot/eqWf+(Slashdot:+Slashdot)
lol
Whichever side of the debate you're on, that's just funny.
M Paquette
Moderator Emeritus
Update does nothing, virus already has a workaround that defeats Apple's update.
New MacDefender Defeats Apple Security Update - Slashdot
lol
Whichever side of the debate you're on, that's just funny.
That's /.'s opinion. About as useful as a debate on 4chan.
Meanwhile, the automatic update of the safe downloads filter, new with this security update, gets a push notification, updates, and quashes the new hack.
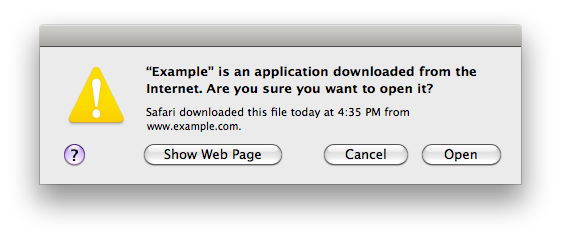
Oh, and if you see this dialog when you weren't expecting it, click Cancel.

ERD50
Give me a museum and I'll fill it. (Picasso) Give me a forum ...
Update does nothing, virus already has a workaround that defeats Apple's update.
New MacDefender Defeats Apple Security Update - Slashdot
I was going to comment after M Paquette posted about the update to track this. Since this is a "social engineering" malware, it will be a cat-and-mouse game if the offenders want to keep trying. Using my earlier analogy:
if a stranger knocked on your door and you gave them the keys and access code to your house, along with your vacation schedule.
So all Apple can really do is what would be called 'profiling' if we were dealing with people. Something like, 'well, the last malware was wearing a blue jacket, and black jeans, so we won't let any people dressed like that knock on your door'.
While it might not be politically correct, as some have said, 'It's hard to stop user stupidity with a technological solution.' - Oh, that was you!
lol
Whichever side of the debate you're on, that's just funny.
Umm, no. I never thought malware, viruses and such on any computer were 'funny'. In fact, I'm furious that in the early days of the internet, they didn't pounce on offenders and make it clear that there was going to be a high price to pay for sending trash to your kid's email accounts and so forth. I think it's sad, and not something that depends on being on any side of any debate, IMO.
-ERD50
M Paquette
Moderator Emeritus
I was going to comment after M Paquette posted about the update to track this. Since this is a "social engineering" malware, it will be a cat-and-mouse game if the offenders want to keep trying.
Exactly. The exploit relies pretty heavily on people doing things that are generally considered unwise these days. Apple can do a reasonable job of making delivery difficult for Russian 'payment service company' ChronoPay, the folks who have been collecting from users scammed by Mac Defender and derivatives.
Ultimately, though, people just need to be aware that there are bad actors out there. Always use caution when opening E-mail attachments and content downloaded from the Internet. When the computer gives you a warning, pay attention.
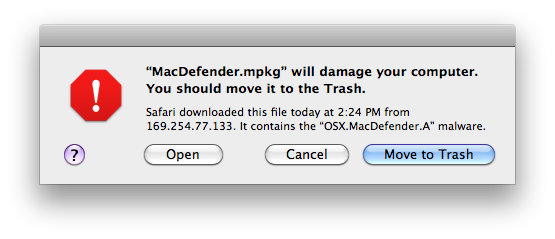
If the Bad Guys manage to download an Evil App, the quarantine system in Mac OS X will notice the app when it tries to run. You'll get this dialog which lets you cancel launching the app. It may also offer to show the web page where the app came from, if known.
M Paquette
Moderator Emeritus
While it might not be politically correct, as some have said, 'It's hard to stop user stupidity with a technological solution.' - Oh, that was you!
Nobody has come up with a patch yet for user fear and gullibility.

I suppose that also means Variable Universal Life and timeshare salespeople are safe for now.
arebelspy
Full time employment: Posting here.
- Joined
- Apr 26, 2011
- Messages
- 625
M Paquette said:That's /.'s opinion. About as useful as a debate on 4chan.
Huh. I wasn't aware people had such a low opinion of /. Care to share why? I have no dog in this fight, I'm just curious.
And actually, if you read the comments on the link, most of them agree with you, and point out that Apple will have the "new" version fixed automatically now once the antivirus checks for it's definition update.
ERD50 said:Umm, no. I never thought malware, viruses and such on any computer were 'funny'. In fact, I'm furious that in the early days of the internet, they didn't pounce on offenders and make it clear that there was going to be a high price to pay for sending trash to your kid's email accounts and so forth. I think it's sad, and not something that depends on being on any side of any debate, IMO.
Fair enough. I tend to find amusement in things, rather than letting them anger me, and it's not something that depends on being on any side of any debate, IMO.
M Paquette
Moderator Emeritus
Apple can do a reasonable job of making delivery difficult for Russian 'payment service company' ChronoPay, the folks who have been collecting from users scammed by Mac Defender and derivatives.
Followup: The head of ChronoPay, Pavel Vrublevsky, has been arrested in Russia on suspicion of hiring someone to launch a denial-of-service attack against one of his company's main competitors. The arrest is the latest in a series of high-profile actions against people and groups around the world suspected of being involved in the global cybercrime ecosystem.
https://threatpost.com/en_us/blogs/head-russian-payment-processor-chronopay-arrested-062511
https://threatpost.com/en_us/blogs/...i-intl-authorities-results-two-arrests-062311
Similar threads
- Replies
- 38
- Views
- 2K
