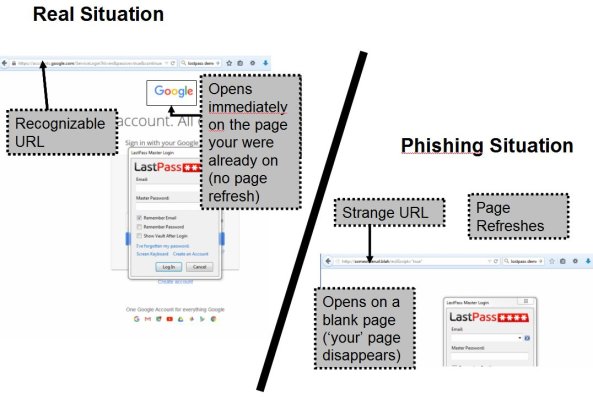
As scary as this phishing attack is, I do think that most of us would realize something was amiss when the master password dialog appeared on a blank page and not on top of the page we were on (see image).
The reason why clicking on the LastPass icon in the brower's tool bar is safe is that there is no vulnerability there. I'm sure hackers have tried, but they have not succeeded in getting their code to run when you click on the LastPass add-in button. Contrast that with clicking anything in the view port. THAT is where the phishing problem is.
Correct. If you don't want to get phished, follow Rule#1: only type your master password only if you specifically asked for the login dialog from the add-in button. Problem solved.
Since the encrypted vault is in the cloud, it makes the master password more valuable to a hacker than, say, a vault on a thumb drive.
You don't need to hamstring LastPass! True, a hacker could put a green bar up. The worst they could do is not put that site's password in the vault. Under your scenario, they've already got that site's password. Follow Rule#1 and go on with life as-is.
You can limit IP by country, shut off notifications, etc, if it makes you feel better, but if you think back to the original phishing problem, and really understand it, you'll realize it's not necessary to change the configuration at all. Just follow Rule#1.
 I have been using LastPass for the last 5 to 6 years and like it very much. I had planned on only using the button on my browser, but now that I have turned off all of the notifications, I don't even need to be tempted to click on anything.
I have been using LastPass for the last 5 to 6 years and like it very much. I had planned on only using the button on my browser, but now that I have turned off all of the notifications, I don't even need to be tempted to click on anything.