Sunset
Give me a museum and I'll fill it. (Picasso) Give me a forum ...
After the massive attack of heartbleed bug a couple years ago, I started using the password manager Keepass. It has given me tremendous peace of mind, means I don't have to remember any passwords, and greatly reduces the time needed to access my protected sites. Keepass is locally stored (versus stored in the cloud like password manager lastpass). I don't store the password manager on my computer, but rather on four identical back-up thumb drives, two of which are protected behind an encrypted vault and kept at home, and two further back-up drives which are not encrypted are kept in my safe deposit box.
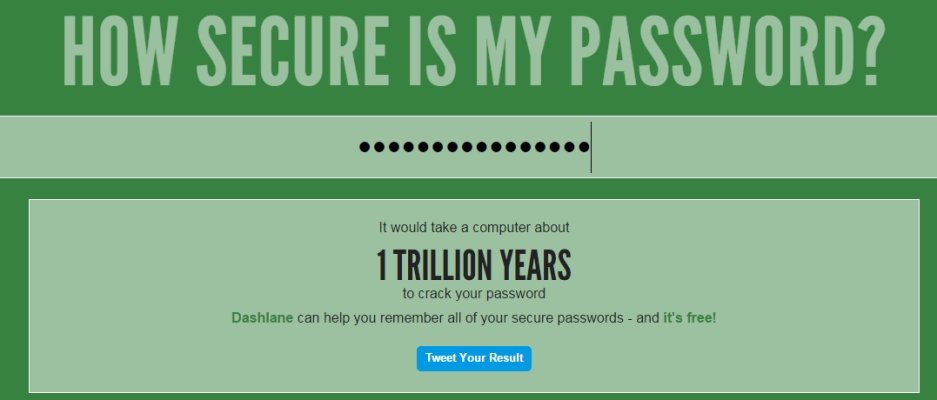
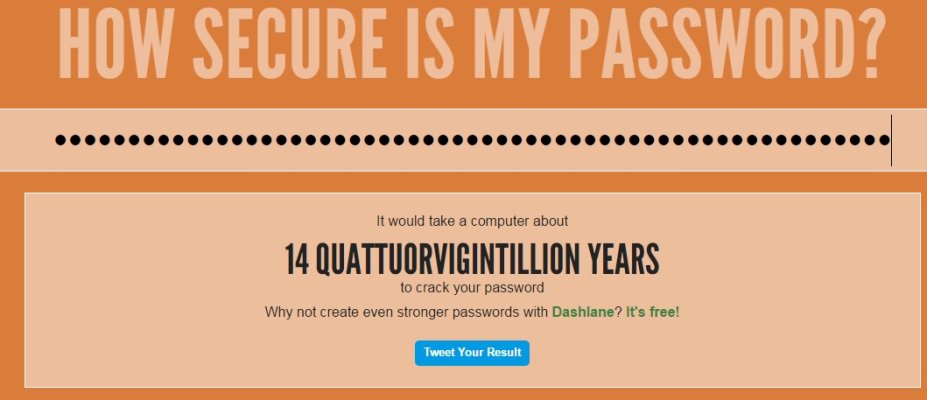
Keepassgenerates all of my passwords of a length as long as any site will allow (all of my passwords are very long and complex) and Keepass is only accessible with one global password, which I do not have written down anywhere. I've tested this global master password and it would take almost a hundred thousand years for my password manager to be hacked. The only two people know in the world know the global password are myself and my executor.
I would never use any password that is only eight words long, nor would I use one that doesn't contain numbers, special characters, and upper and lower case characters. Experts have advised strongly against using any password for more than one account, as this is one of the first things hackers look for. There has been considerable debate regarding password managers that are locally stored (as in on one's hard or thumb drive) versus stored in the cloud; however, I am personally extremely uncomfortable with cloud-based password managers and would never use them.
+1
Easy to use, works reliably for years. I have over 200 Unique passwords.
It also provides a notes section so you can store the crazy unrelated answers to the security questions:
Example - What is your first pets name: Answer: AlexanderTheGreatWasAWhipperSnapper