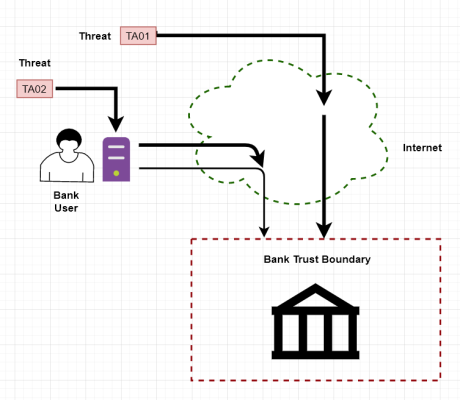
Very much more complicated. I've yet to hear any specifics as to how on-line transactions increase my risk. Like, what exactly constitutes the "threat" hypothesized in the diagram?
Of course a lot depends on the person. If you create weak passwords, share them with others, post them or save them somewhere obvious, then another individual may take advantage of you. But that's not what this thread is about. We're talking back-end hacks, which you have no control over.
I'll also add that at the individual level, it's far more likely that someone will simply provide their account information to a phone scammer. Which of course would have nothing to do with whether or not they made legitimate online transactions.
Yes, I remember F-PROT. And I've done first-, second- and third-level user support. You'll get no argument from me about the damage a clueless user can inflict.
But again, we're talking big picture. Assuming I'm not handing out my information to scammers, the risk isn't coming from MY chair. Maybe some low-level employee at the financial institution or one of their contractors, but that's not something *I* have control over. Nor is it something that *I* will be held accountable for. If it's their mistake, they will take the loss. Anything short of that would undermine our entire financial system.
I remain unconvinced that I'm increasing my risk by using online transactions.