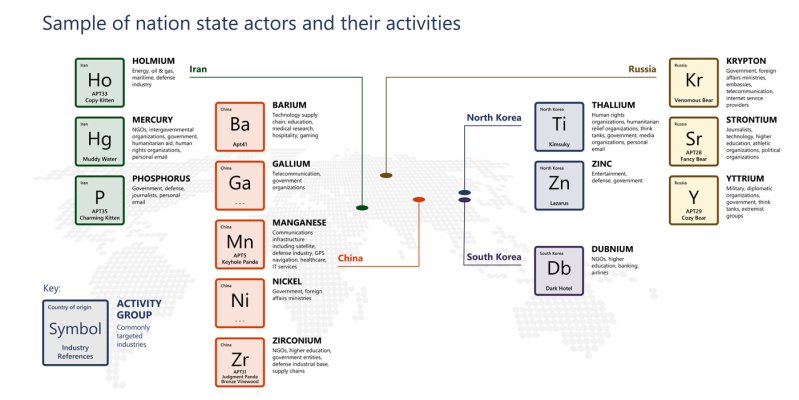
This huge Russian hack (databreach?) appears to be ongoing and "they" don't even know where it's been and what the status is.
My Big Banker relative advised changing passwords, but he doesn't even know if banks are affected - have any of you heard of that?
And it isn't even apparently about money (well, everything is about money eventually).
I've seen very little advice from anywhere, which in itself is alarming. Nothing from Lastpass - have any of the password managers communicated? The silence out of the Executive Branch is alarming. Can they really not know this much?
Any thoughts, advice?
*edited title to make the topic clearer. Not even sure if I should call this a data breach.
My Big Banker relative advised changing passwords, but he doesn't even know if banks are affected - have any of you heard of that?
And it isn't even apparently about money (well, everything is about money eventually).
I've seen very little advice from anywhere, which in itself is alarming. Nothing from Lastpass - have any of the password managers communicated? The silence out of the Executive Branch is alarming. Can they really not know this much?
Any thoughts, advice?
*edited title to make the topic clearer. Not even sure if I should call this a data breach.
Last edited: