Katsmeow
Give me a museum and I'll fill it. (Picasso) Give me a forum ...
- Joined
- Jul 11, 2009
- Messages
- 5,308
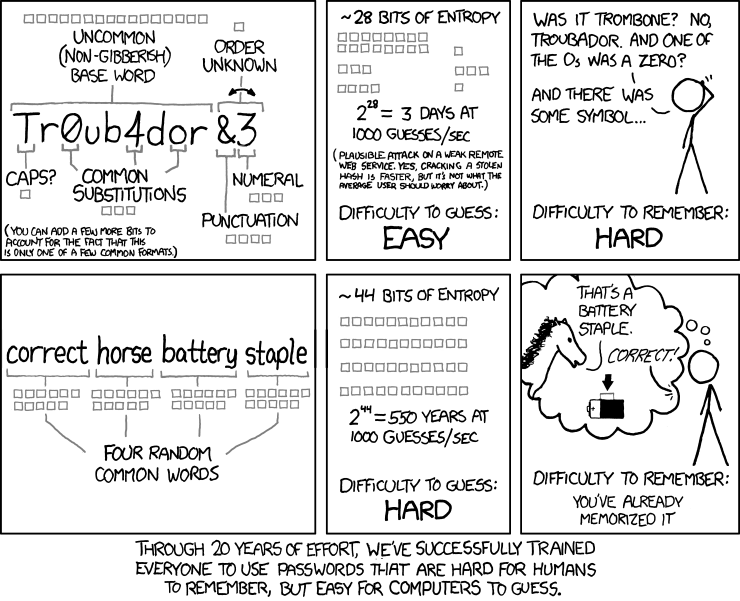
On passwords..
I remember two passwords. One for my password keeper and one for my email accounts. All other passwords, I use a random generator by my password keeper to create secure passwords. Also, now even with my user ids, a portion of that is randomly generated for safety.
For me, trying to remember password combinations that are safe is just too taxing on the brain when some require special characters, and some do not, and once you have one in memory, the password may expire.
The thing that has been stopping me from using the password generator is that I don't always want to look at passwords from my home computer. I may log in from my office notebook or from my own notebook when I leave town.
Roboform is nice and I use the one that can be used on one computer. They have a couple of other options. You can get Roboform everywhere which you can use on any computer since the password info is uploaded. DH and I both feel uncomfortable with our passwords being uploaded somewhere although maybe we are being unreasonable.
You can also get Roboform 2Go which lets you put the Roboform data on a USB drive and then you plug that into any computer you use. What I don't like about that (beyond buying a new program) is what if you lose the USB drive? On the other hand, it isn't useful to anyone if they don't have your master password. So...just not sure which way to go on that.